Blog post
Synthetic Fraud And ID Theft: Treatment Strategy Considerations For Financial Institutions
Max Blumenfeld, Co-Founder, COO and Head of R&D
Published
December 1, 2022
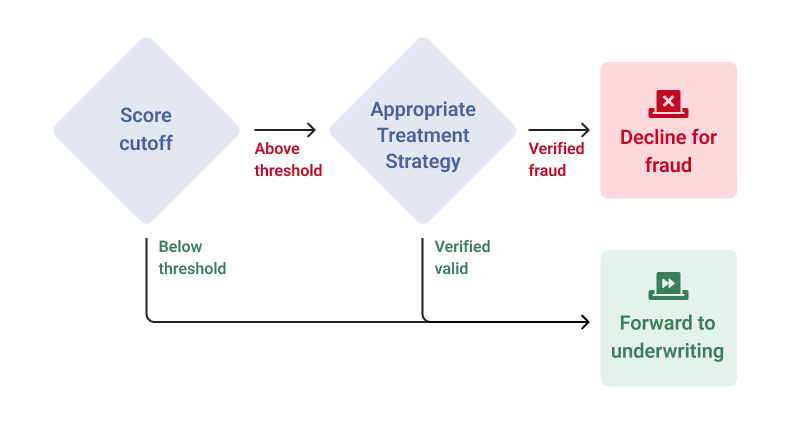
What is the right risk treatment strategy to implement when your fraud detection solution flags a high risk application?
As risk and fraud teams know, there is no one-size-fits all answer. To be effective, a treatment strategy must be tailored to the specific risk being flagged. In the case of high risk applications, that assessment should rely on appropriate tools that target specific types of fraud so that the respective treatment strategies can address the specific risk.
The objective of a precise and well-calibrated treatment strategy is to appropriately counter the risk without creating unnecessary friction for the user. Generic treatment strategies will generate worse outcomes for rejecting true fraud and customer approval rates. Off-the-shelf step-up verification will fail to stop certain types of fraud. For example, KBA and traditional document verification will not be an effective treatment for synthetic fraud. Implementing dynamic authentication strategies based on the risk level posed by the application is the preferred method to keep fraudsters off guard since they won't know in what way they will be challenged.
Synthetic Fraud Treatment
SentiLink got its start by detecting synthetic fraud. This type of fraud refers to an application in which an applicant supplies a name, DOB, and SSN combination which does not correspond to an actual person, and would not be recognized by a "source of truth" like the Social Security Administration. Whilst some fraudsters will create entirely fictitious identities based on random combinations of PII, it is often the case that an actual consumer will apply for credit with their true name and DOB, but the wrong SSN, leading the financial institution to attempt to pull a credit report tied to the synthetic version of the real consumer. One unique challenge posed by this type of synthetic fraud is that traditional treatment strategies do not apply. For example, the individual attempting this type of fraud:
- will have a government issued ID with their name and DOB
- will have a phone that’s been tied to their name
- will have an email that’s been tied to their name as well
- will likely know all of the KBA type questions that could be generated from their fictitious identity since they created the identity
The appropriate treatment strategy for synthetic fraud is eCBSV or some other form of name, DOB, and SSN validation against source of truth databases (4506-Ts and SSA-89 forms will suffice).
ID Theft Treatment
When combating traditional ID theft, aligning treatment strategies to present risk is important for both reducing fraud and ensuring a good customer experience. In the past, a physical address not matching the applicant’s was the clearest signal of identity theft as that was the means by which the consumer (or fraudster) would control access to the account (i.e., receiving a debit card in the mail). Today, however, the present risk is much more closely linked to control of a phone and/or email address by the fraudster. For instance, when an application for a credit card includes a brand new email address like "JohnDoe123456@gmail.com," the applicant is likely able to control that email and therefore successfully complete an OTP, or click a verification link sent to that address. However, that does not mean the application is not fraudulent.
In these scenarios, a fraud team should focus on two key characteristics of the email address and phone number provided on an application: Association (confirm they are linked to the applicant) and control (validate that they are controlled by the applicant).
Association is typically determined by a third party data provider returning a name associated with the phone or email. Critically, institutions should also focus on the time of association (i.e., the amount of time an email or phone has been linked to the person). This flags if a fraudster has recently established an email or phone in the name of the victim. This is a common tactic, whereby a fraudster applies for a phone in the name of the victim or opens a new email address which contains the victim’s name to establish association thereby controlling the contact instrument to receive the OTP.
We’ve included below a potential workflow for onboarding for ID Theft specifically:
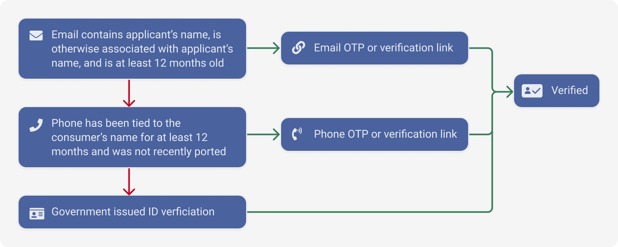
Some institutions may consider swapping email and phone OTP depending on whether a consumer’s username is their email address or phone number. Oftentimes, the first item in the proposed workflow is “free” since FIs typically verify a phone or email address for deliverability purposes.
The Optimal Treatment Strategy
Treatment strategies must be effective against specific types of fraud whilst being sustainable for the organization that is implementing them. Designing the optimal treatment strategy starts with identifying the specific type of fraud being "treated," but must also be shaped by a number of factors specific to the organization:
- Indicator precision of the detection solution that is in place (i.e. true positive/false positive rates)
- Economic costs of false positives and false negatives
- Application channel
- Other constraints, such as: technology, customer communication options, channel partnerships
Selecting appropriate treatment strategies that consider these factors is essential to achieving low identity fraud rates while providing a positive and secure customer experience at a time when it is most critical - the beginning of the relationship.
For more information on combining high precision scores with appropriate treatment strategies and how we can help, you can reach us here.
________________________________________

Max Blumenfeld is Co-founder and COO of SentiLink. Prior to SentiLink, Max led Risk Operations and Fraud Data Science at Affirm. Max holds a degree in mathematics and economics from the University of Chicago and was named to Forbes’ 30 Under 30 list in 2020.
Related Content

Blog article
April 3, 2024
Tips from a Fraud Fighter for Spotting Assumed Identity Abuse
Read article
Blog article
February 29, 2024
Reducing Complexity in Model Risk Management with Attributes
Read article
Blog article
January 18, 2024